Access Manager
Key Features
Get to Know the Underlying Principles Behind the Access Manager
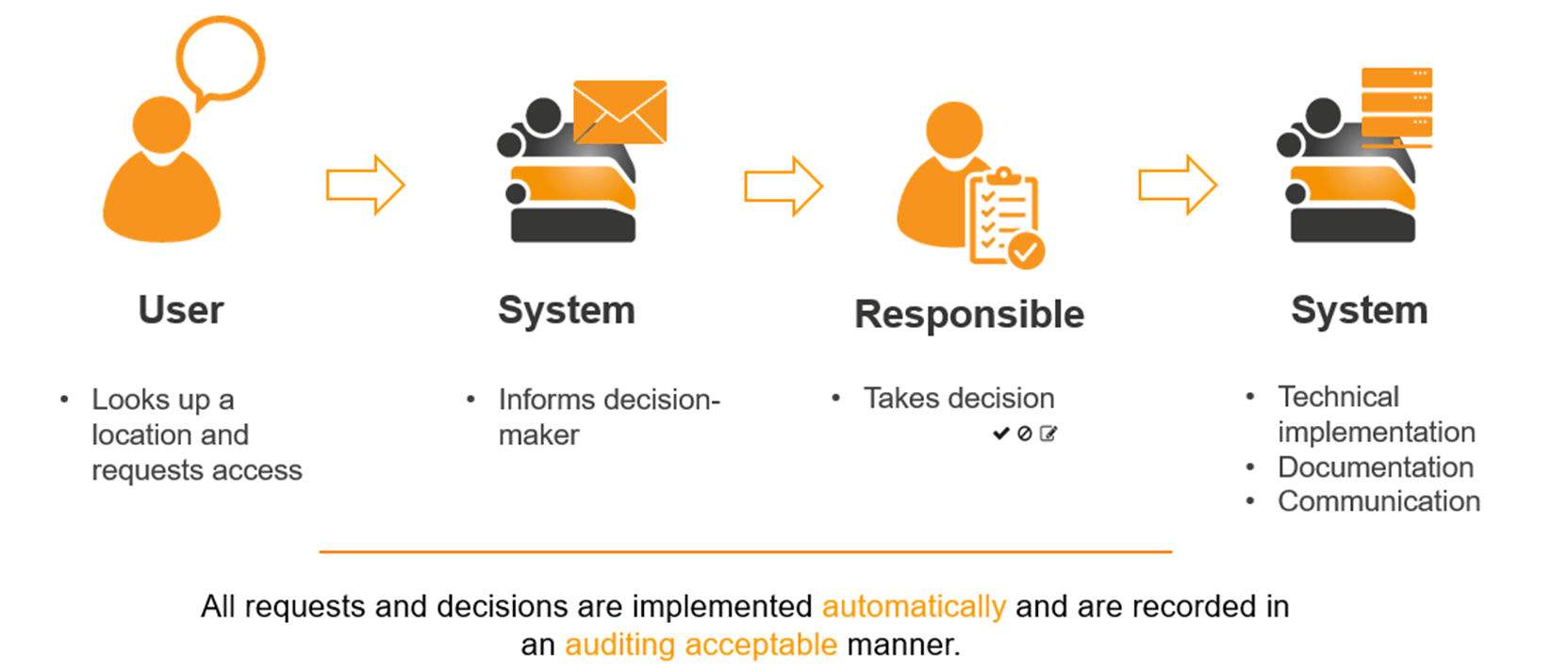
Field-proven since 2008, the Access Manager automates your access management– from assigning permissions to the end of authorized access. The software solution establishes privacy by default and design, supporting the principle of data minimization according to General Data Protection Regulation. The permission situation is continuously monitored and every permission change recorded. This streamlines your clearance workflow and guarantees an audit-proof log of the permission process.
The key features of the Access Manager are an integral aspect of the entire software, forming the basis of clean and reliable access management.
Learn more about the underlying principles of the Access Manager:
Autocorrect of permissions
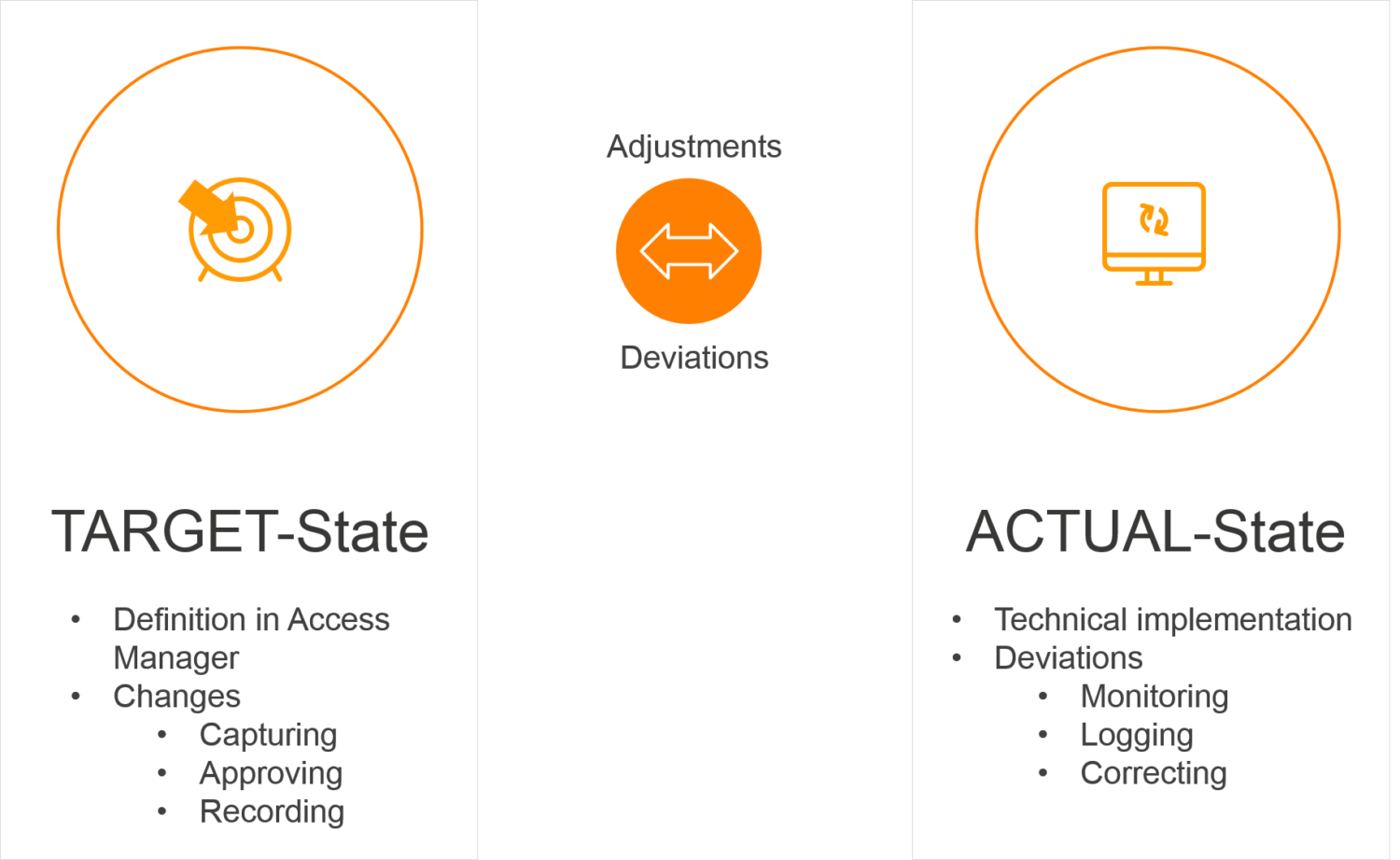
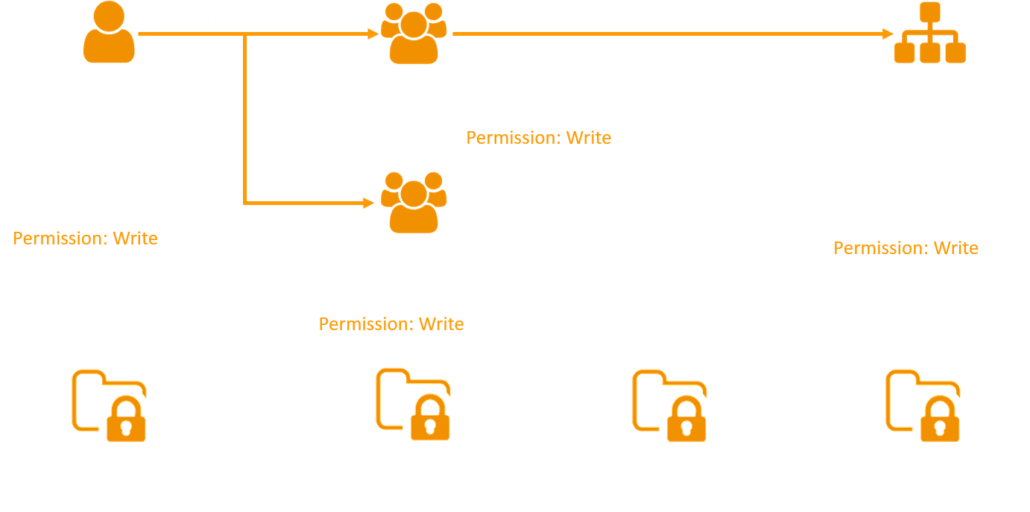
Following the need-to-know principle, a user should only receive as many permissions as they require to fulfil their current tasks. In practice, however, more and more extensive permissions accumulate over time, although most may no longer be needed. Existing permission systems may not even allow a clear delineation of permissions – or they over-simplify to reduce the manual maintenance required. The Access Manager closes the gap between the seemingly contradictory objectives of ensuring data security while keeping maintenance low.
Definition of target permissions in the system
The key difference from manually administrating NTFS permissions via AD groups is that the Access Manager becomes the primary data source for target permissions in the file system. All changes – such as the issuance or removal of permissions or changes to existing NTFS permissions – are captured via the Access Manager and the decision process logged.
Implementing NTFS permissions according to best practices for Microsoft file servers
The Access Manager subsequently adjusts the actual technical state of NTFS permissions to the desired target state. The best practices for Microsoft file servers are applied to the complete technical implementation including the maintenance of Active Directory groups, group memberships, and the assignment of NTFS permissions.
Assigning temporary NTFS permissions
In contrast to NTFS access management with standard tools, the Access Manager offers the option to set up time limits for NTFS permissions in the file system. If the time limit isn’t extended before expiration, the granted permissions are automatically withdrawn on the relevant date. This feature is ideally suited to temporary project work as well as external staff with frequently changing areas of work such as participants of trainee programs or apprentices.
Request our product presentation and get to know the Access Manager with all its advantages.
.
Self-Service for Data Controllers and End Users
A key component of our solution is the self-service concept, allowing various departments and end users to be involved in the access management process without needing an IT background. This is a principle that runs throughout the Access Manager. No matter when creating a new protected directory, requesting access to an existing SharePoint site, preparing analyses on existing access permissions or reset a forgotten password – everything can be taken care of without consulting IT administrators and all in accordance with the organization’s standards.
1
2
3
4
5
6
1
Targeted access only to required functions
2
Simple request of authorizations
3
View, change, decide requests
4
Information about inquiries and actions by mail
5
Clear and understandable overview of enquiries
6
time limitation directly at the time of approval
Regular Permission Review with Reapproval
949859969
Your employees receive additional permissions every day – do they really need them all?
According to the need-to-know principle, employees should only obtain the access permissions they actually need. This approach is often applied to the assignment of permissions but forgotten again when it comes to eventually removing the permissions. Employees therefore gradually accumulate permissions the longer they remain at the company – regardless of whether the permissions are still required after years of service.
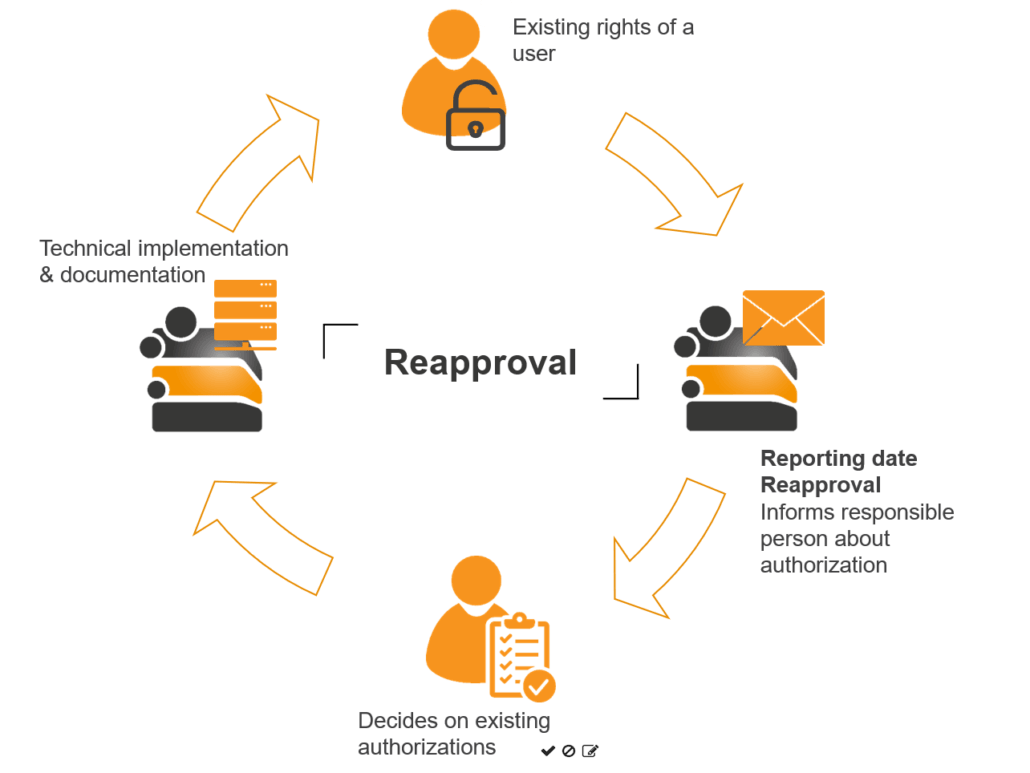
To prevent this uncontrolled growth in permissions, auditors recommend recertifying or reapproving permissions. In doing so, data controllers should regularly review the existing permission situation. But they’re often not especially happy to take on this task. For them, it means extra work and having to get to grips with technical details and mountains of documents full of complex matrices.
Keeping existing hurdles for data controllers as small as possible is therefore essential for a successful recertification process.
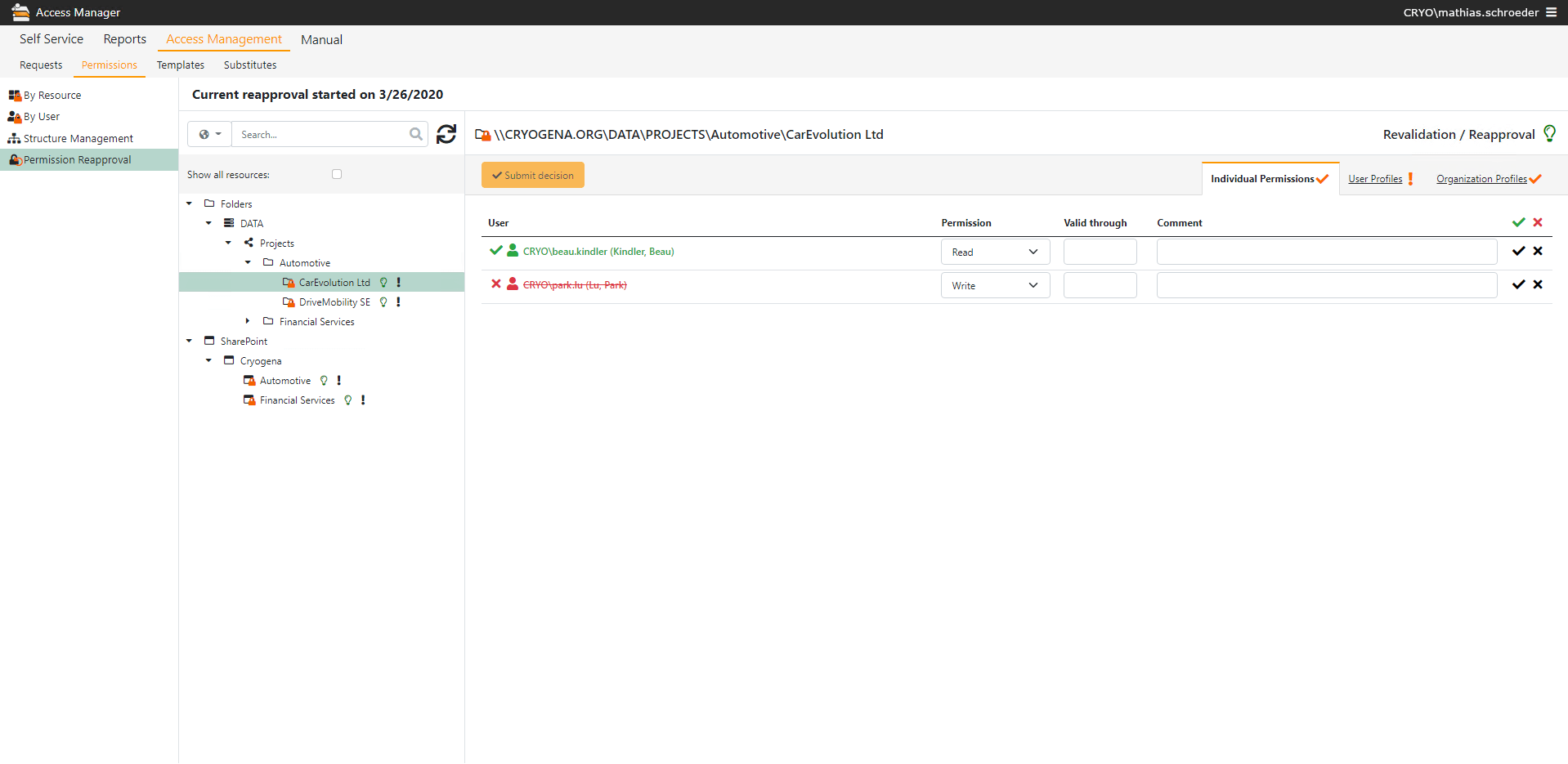
This is where the Access Manager comes in with the integrated Reapproval system. This process also benefits from intuitive use via a browser, enabling straightforward and transparent access management.
This way, the recertification process is made as simple as possible for data controllers. They’re neither confronted by mountains of paper nor unfamiliar IT details, allowing them to perform the task effectively. The option to set multiple data controllers per resource also allows the work to be spread among several people.
Profile Management for Presenting Organizational Permissions
Need-to-know vs. scattergun approach
Staff and structural changes within an organization regularly necessitate fine adjustments to the permission situation in the various IT systems. The research, coordination and adjustment work involved takes up substantial resources in decision-making by data controllers and implementing changes to grant, alter or remove numerous user permissions.
To assign new permissions, the need-to-know principle is often rejected in favor of the scattergun approach:
Permissions are assigned generously at the departmental level or reference users with similar tasks are used as a basis to roughly determine new sets of permissions. In this process, the individual permissions of the reference user are frequently adopted without further thought. Or, the ability to assign individual permissions is prevented throughout the organization, occasionally leading to unconventional (and largely insecure) forms of data exchange between users.
In order to support staff changes effectively, the profile management of the Access Manager offers the ability to map organizational structures – such as departmental and activity assignments – by creating corresponding user profiles in the system. This combination of users and resource permissions in a profile means only a profile adjustment by the superior is necessary in the event of a change in activity. Individual permissions can also be assigned, which unlike the approach with reference users are not simply transferred without thought. This ensures that the user only obtains the permissions they actually need.
User Provisioning – Create, Change and Manage Users
Staff and structural changes within an organization often make it necessary to create or deactivate employee accounts in the Active Directory. What’s more, the permission situation has to be finely adjusted in the various IT systems.
The Access Manager user provisioning enables you to combine account creation and deactivation with the assignment of profile or personal permissions in a single step. After creating a new AD account, administrators can thus define profile memberships on the same page and assign personal permissions. Security groups, home directories and the management of Internet access via firewalls / proxy servers are also possible. When an employee leaves the company or changes departments, meaning existing permissions and roles are no longer required, all owner and controller roles, profile memberships, and personal permissions of the user can be removed and a successor named with a single click.
User Provisioning and Identity Management is rounded off with the option to reset an AD account password at the request of an employee, the subsequent configuration of expiration dates, enable and disable OCS for users and the configuration of account information (such as telephone number and department membership) for displaying to end users.
Audit-Proof Documentation of Actions
All actions performed with the Access Manager are meticulously logged and can be viewed by authorized individuals at any time. Plus, the audit functionality enables you at any time to precisely retrace which changes were implemented when, by whom, and for which resource. You gain full control of the activities in your systems. You can also find out whether unintended permissions were assigned or removed in the file system, which you did not authorize.
This core feature of the Access Manager makes it possible to safeguard your company’s internal regulations, contractual agreements, and statutory requirements in terms of file access permissions, and maintain audit-proof records.